Analysing and understanding website attacks
All devices directly connected to the public Internet are regularly probed. The source is commonly an automated script of some type – depending on its purpose it could be described as a scanner, crawler, scraper, spider, bot or more. It’s important to remember that not all bots are malicious – many are in fact necessary such as the Google bot that compiles search data. I’m not going to define or categorise the assortment of “scripts” running loose on the internet – for those interested though I have included some relevant links further below.
In this blog we will take a look at some of the malicious bots we see interacting with a real live web server running WordPress. We will observe what’s going on by analysing the web server logs and look at the packets themselves.
Weblogs, in our case Apache server logs, show the meta data of connections made to it, including the source IP, date, time-stamp, action taken, URI and user-agent string. You can find more details on the format here.
Let’s take a look at one of our logs (click images to embiggen):
We can see that a connection has been made to the WordPress login page (wp-login.php) from 91.210.147.100. Using Geo IP Tool we can get an idea of the source location – Ukraine, which is not where we would expect to see administrator connections coming from in this case. We can also guess the attacker is running on Windows 10 and using a Chrome browser from the User-Agent (UA) string. We won’t read too much into the UA string as it can certainly be spoofed as we will see later.
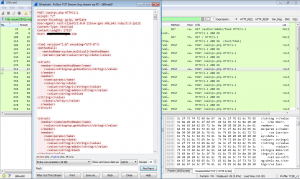
The weblog is interesting, but it cannot show us what credentials were sent by the user. Let’s check our packet trace for more information:
It shows the username entered was “se13” and the password as “secret”. Luckily these credentials are incorrect.
If we continue to search for this IP we find it regularly trying to login and work through a dictionary list of passwords.
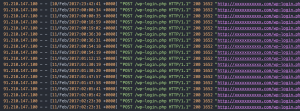
This is typical brute force bot behaviour. It is likely the aim of the attacker is to gain access to the WordPress site and upload their own content – usually pharmaceutical spam. Rather than pay for their own hosting, e-criminals hijack other WordPress sites providing them with an additional form of cover in the short term.
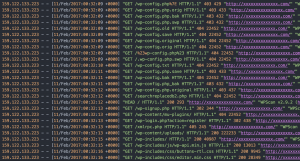
Let’s take a look at the packet trace from another IP address that is generating a lot of logs; 159.122.133.223 according to geoiptool is Italy.
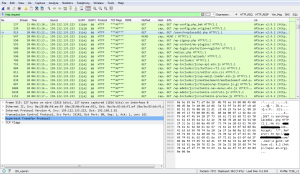
The attacker behind this scan is using the WPScan tool as can be seen in the user-agent string.
WPScan is a brilliant WordPress vulnerability scanner. It will enumerate the WordPress install and the plugins and themes the site is running, and the tool will highlight any out of date packages, especially those with known vulnerabilities.
The attacker has been heavy handed in their use of WPScan and has caused a lot of noise in the web logs.
This attacker has also attempted to access the WordPress site using brute force. The packet trace shows repeated login attempts using the username “admin” and passwords including “qwerty”.
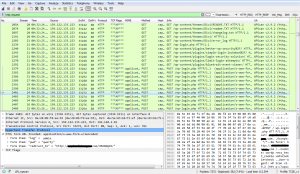
The above brute force attempt shows the use of word lists. Word lists are a favourite among hackers because they work! As we’ve said before, you should always use a non-linear password for exactly this reason.
The next heavy hitter in our web logs is 169.57.0.215 which appears to originate from Mexico
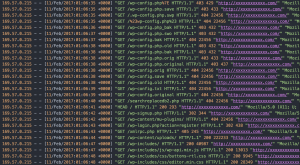
This series of GET requests looks very familiar. It is almost identical to the previous web logs by the attacker using WPScan. This time the UA string is “Mozilla/5.0 … Gecko/20110430 shadowfox/7.0”. I think it’s a safe bet to assume this attacker has also used WPScan but spoofed the UA string.
So far the password brute force attempts we have seen consist of one username and one password in each request and they have been scripted so that many login attempts can be tried in a short space of time. However we have also seen that this type of attack makes a lot of noise and leaves a large footprint in the web logs that can be easily identified. There is however a WordPress attack where hundreds of passwords can be tested in a single request. This is known as the XML RPC brute force amplification attack – see here. This vulnerability came out in late 2015 and affected most WordPress installations at the time.
Searching through the logs for “POST /xmlrpc.php” brought up an interesting entry – 162.216.46.132 likely located in Texas, United States.
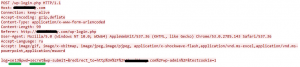
This single log entry is very different to the pages of login requests we see in the previous attacks. Let’s take a look at the packet trace to understand what is going on.
Looking inside the POST data you can see multiple credentials being sent to the web server, such as admin / chelsea and admin / black. The full list of credentials contained 500 unique passwords all inside the single request. Being able to test hundreds of passwords in a single request makes the likelihood of successfully brute forcing a password significantly more likely.
How to protect your web connected server?
To protect your web servers and other internet connected devices:
- Use a strong password – https://www.thecybersecurityexpert.com/ask-cyber-security-expert-cyber-security-hard/
- If supported, enable 2 factor authentication – https://www.thecybersecurityexpert.com/ask-cyber-security-expert-two-factor-authentication/
- Regularly patch and update – https://www.thecybersecurityexpert.com/web-site-security-an-introduction/
- For enhanced security – monitor your assets, servers and data – https://www.thecybersecurityexpert.com/so-youre-in-charge-of-cyber-security-part-the-2nd/
Bonus question
What do the following attacker IP addresses have in common?
159.122.133.223 (Italy)
169.57.0.215 (Mexico)
162.216.46.132 (United States)
We provide a website monitoring and protection service which will protect your website from the types of attacks we’ve discussed in this blog. Get in touch for more info.
Find us on twitter, or use the contact form.
Thanks for reading
Jag (@jagjag6)
References:
https://www.cybrary.it/glossary/
https://en.wikipedia.org/wiki/Internet_bot
https://support.google.com/webmasters/answer/182072?hl=en
https://www.europol.europa.eu/activities-services/public-awareness-and-prevention-guides
https://httpd.apache.org/docs/2.4/logs.html#accesslog
https://github.com/wpscanteam/wpscan
https://crowdshield.com/blog.php?name=WordPress-xml-rpc-brute-force-amplification-exploit