Ask The Cyber Security Expert: How do I know if an email is spam?
As The Cyber Security Expert I am often asked, “how do I know if this email is spam or not?”, to which I answer “if you have to ask, then it’s spam”. Slightly flippant I appreciate, but broadly true. Any email exhorting you to do something, be it check for a problem with an account, click on a link or open an attachment is quite likely to be spam, and you are much better off just deleting it. If you ever are actually worried about the status of your online banking/Amazon/iTunes account the best thing to do is visit the site directly (by which I mean type the web address into your browser, or use your bookmark), log in, and see if everything is ok. Or phone or email the company. But never, ever click on links.
Anyway, since it is a common question I thought I’d walk through a process for deciding if email is suspicious or not.
The Email
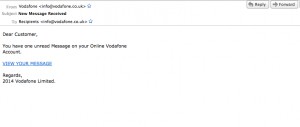
Last week I received this [click to embiggen]:
At first glance all seems well; the sender is apparently Vodafone. However there is one dead giveaway that this is probably malicious – I’m not a Vodafone customer. However, even if I were this does not look entirely legit. It’s a bit basic for a message notification, and it seems unlikely Vodafone services really sign off with “2014 Vodafone Limited”. Finally it makes no mention whatsoever of me, and doesn’t use my name – it is a plain, generic email with nothing to suggest the sender knew anything about me, the recipient.
So, it is clearly slightly suspect, even if you were a Vodafone customer. But how to check further?
The first thing to check is the embedded link (the text in blue in the image). Does that actually take you to Vodafone or not? And you don’t want to click on it to find out. An easy way to check is to hover the mouse pointer over the link and see if anything further is revealed. You should see details of the destination website appear, either by the mouse pointer or (as per my mail client) in the status bar at the bottom of the email:
That does not look like a legitimate Vodafone website. At this point your casual investigation can stop, and you can delete the email. This is very clearly not actually from Vodafone and is either trying to steal your Vodafone credentials or trying to install something malicious on your computer. Go no further. Here be dragons.
Email Headers
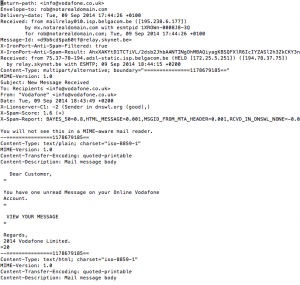
If you want to check the real source of an email, you need to look at the email headers. The way you do this will depend on your email client. I’m using Mozilla Thunderbird, and can do this by selecting View -> Message Source. Outlook varies depending on the version of Windows and Outlook you are running. There is guidance here for Outlook 2010. For other versions open help and search for ‘message headers’ or ‘message source’. Once you have found it you will be presented with something that looks like this:
In this you can see the mail headers up at the top, which describe the path across the internet the email has taken from recipient to sender, and further down you can see the sender email, followed by the body of the email (the text you would see in your email client). Looking at the raw text above we can see the sender is supposedly Vodafone, as was trustingly displayed by my email client:
However, looking above that section reveals that this email actually came from what appears to Belgacom ADSL IP address pool:
In other words, this email came from the compromised home computer of a Belgian internet subscriber. That is absolutely nothing to do with Vodafone, and supports our hypothesis that this is a spoofed email sent for malicious purposes.
What have we learned?
Never click on links or open attachments. I can’t say that often enough. If you find yourself wondering if there is something fishy (or even phishy) about an email then there almost certainly is, and you should delete it. Almost all elements of email can be spoofed – even some parts of the message headers, so just because an email appears to come from your bank it doesn’t mean it actually did. This post describes some basic steps you can take to verify the legitimacy of an email, but always if you have even the slightest doubt, play it safe.
In a future post I’ll look at how you can deal with suspicious attachments to email, and I’ll show you some really useful online tools which can make this sort of investigation a lot quicker and easier.
As always, if you have questions please get in touch! Find us on twitter, or use the contact form.
The Cyber Security Expert