Getting the Most Out of Wireshark
What is Wireshark and who uses it?
As described on wireshark.org
“Wireshark is the world’s foremost and widely-used network protocol analyzer. It lets you see what’s happening on your network at a microscopic level and is the de facto (and often de jure) standard across many commercial and non-profit enterprises, government agencies, and educational institutions.”
Simply, Wireshark is a great tool for network analysis and it is used by IT professionals all around the world.
Getting the best out of Wireshark
Wireshark is heavily used by Security Analysts and Information Security professionals on a regular basis. I have worked in different Security Operation Centres (SOC) in different industries and I see Wireshark being used all the time but … the default Wireshark layout and view is not efficient for Cyber investigations!
Analysts need to be quick
Based on the interesting, and in my opinion accurate, “Voice of the Analyst Study” report by the Cyentia Institute in 2017. Analysts spend their time on 12 broad activities. Because of the many plates Analysts have to keep spinning, they are only able to spend 25% of their time (on average) on real-time monitoring and triage.
When investigating network traffic, you need to be able to find suspicious / malicious indicators very quickly. Typically you have 30 seconds to decide whether the Alert is a true positive (investigate further) or a false positive (something has been flagged as malicious when it’s not).
There are hundreds of Alerts to investigate, so … Analysts need to be quick!
Configuring Wireshark
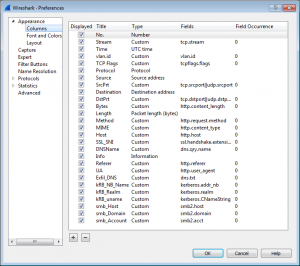
Network flows can be best understood by looking at particular fields. For example in http traffic the host and user-agent fields and the request itself are important. Quickly finding the http response and the content-type are key. The next section looks at configuring Wireshark to show the key fields in http, https, dns, windows smb and authentication traffic.
I have been inspired by Brad Duncan’s work at Malware-Traffic-Analysis over the past 6 years and recommend you follow him on Twitter @malware_traffic. I have borrowed heavily from his Wireshark setup. Thank you Brad.
Edit > Preference > Appearance > Columns
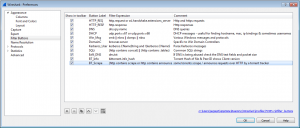
Edit > Preference > Filter buttons
Some tips
- Screen real-estate is a premium. De-select unnecessary columns depending on the traffic being analysed e.g. the smb and authentication specific columns are not useful in pure web traffic captures.
- Learn about Wireshark filters. Think about the protocol (http, ssl, dns etc) and which fields are the most interesting to you from a Security stand-point. Some of my favourite fields and filters are:
-
-
- Show secure secure web server names with “ssl.handshake.extensions_server_name”
- Find SQLi attack strings with “(http contains concat) || (http contains .tables) || (http contains “where’1′”) || (http contains “1’=’1′”) || (http matches “(?i)union”)”
- Looking for data exfiltration and c2 via DNS by viewing the dns.txt values
-
Plugins
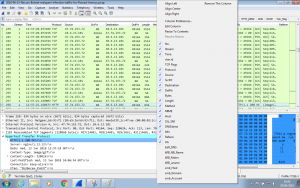
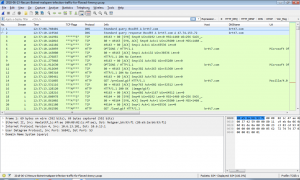
Wireshark is actively being developed by the Wireshark Foundation and the wider community. One of my favourite add-ons is a post-dissector by @DidierStevens which shows the TCP flags in a Snort style format. See the column named “TCP Flags”, it’s easy to see the 3-way handshake in frames 3, 4 and 5. Thank you Didier.
Wireshark setup made easy
Wireshark allows you to save your favourite configuration setups (columns, filters, automatic colour settings) in configuration profiles. If you want to use the configuration I have described I’ll be happy to send you my profile if you get in touch. You can extract the contents to “C:\Users\name\AppData\Roaming\Wireshark\profiles\”, and you can toggle between different profiles by clicking the Profile button in the bottom right-corner.
Thank you for reading, please get in touch in you would like any further information!
Jag
References
[1] https://www.wireshark.org/
[2] https://go.respond-software.com/voice-of-the-analyst/
[3] https://www.malware-traffic-analysis.net/tutorials/wireshark/index.html
[4] https://twitter.com/malware_traffic
[5] https://blog.didierstevens.com/2014/04/28/tcp-flags-for-wireshark/
[6] https://twitter.com/DidierStevens
[7] https://www.wireshark.org/docs/wsug_html_chunked/ChCustConfigProfilesSection.html
Wireshark and the “fin” logo are registered trademarks of the Wireshark Foundation